Companies are all potential victims of computer attacks that can have disastrous consequences. Hackers primarily seek financial gain but also engage in espionage or destabilization activities. They exploit poorly protected, vulnerable or outdated systems, as well as poorly secured data.
In this context, Data Privacy professionals offer a range of organizational and technical cybersecurity services as well as training to help protect you from any cyber threat.
Our cybersecurity services
Organisational security
Technical security
Risk analysis
Risk analysis using the EBIOS Risk Manager method from ANSSI. This method helps minimize the risk of cyberattacks.
Infrastructure security test
Can be internal or external. Simulates an attack on an IT infrastructure.
Information system security policy
Assistance in drafting or updating an ISMS. Based on information systems security standards, this will help reduce the risks of cyberattacks.
Wi-Fi security test
Simulates an attack on a wireless network.
Business continuity plan
Assistance in developing a BCP or DRP. These will help ensure the cyber-resilience of the company.
Web application security test
This test analyses the vulnerabilities of web applications.
Robustness and complexity testing of passwords
Testing all possible combinations of hashed passwords to find the plaintext password.
Our organisational security services
Conducting a risk analysis: EBIOS RM.
The EBIOS RM (Risk Manager) methodology maintained by ANSSI allows for a risk analysis, particularly in the field of cybersecurity.
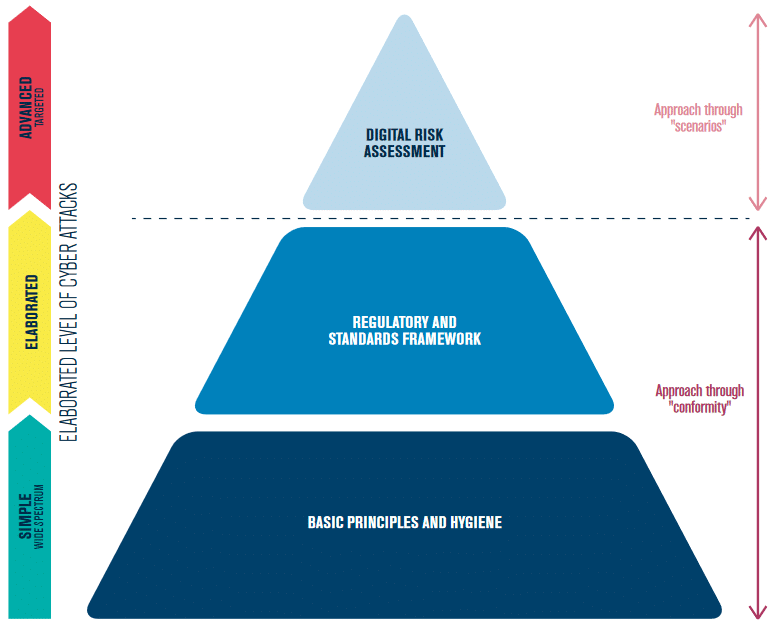
One of the objectives of the methodology is to reduce the probability, likelihood, and impacts of cyber attacks. EBIOS RM aims to obtain a synthesis between “compliance” and “scenarios” by repositioning these two complementary approaches where they provide the most added value. EBIOS RM does not limit itself to a static view (compliance) but integrates a dynamic view (attack scenarios). The approach followed by EBIOS RM is to combine the viewpoint of the cyber attacker and the company.
Data Privacy Professionals offers to assist its clients in the risk analysis. The deployment of the EBIOS RM methodology will reduce their risk of cyber attack.

Assistance in the development of an ISSP
The Information Systems Security Policy (ISSP) is a document describing the security/cybersecurity policy implemented within the company. This document may result from a static view (compliance) or a dynamic view (taking into account the attacker’s point of view).
The ISMS may include, among other things:
– Key Performance Indicators (KPIs)
– Service Level Agreements (SLAs)
– Management of authentication and access control
– Architecture scheme
– Knowledge of vulnerabilities
– Detection and incident taxonomy
Data Privacy Professionals offers its clients assistance in the development of the ISSP. Based on information security standards, this document reduces the risks of cyber attacks.
As it is based on a dynamic view, the ISSP includes a risk analysis. Our approach follows the mechanisms of defense in depth: governance and anticipation, protection, defense, and resilience.
Continuity and Recovery Plan
Writing a BCP/ DRP :
The BCP (Business Continuity Plan) includes a set of procedures, means, equipment, and architectures required to enable the continuity of a company’s activity regardless of the disasters that may occur.
A DRP (Disaster Recovery Plan) refers to various procedures (technical, organizational, security) that enable a company to anticipate, rebuild and restart an information system in the event of a significant disaster or critical incident.
Data Privacy Professionals offers assistance in developing your BCP/DRP. This will enable you to ensure the cyber-resilience of your company.

Contact us for more details
CONTACT USOur technical security services
Penetration testing : Objectives
In a cyber security context, unlike an audit, whose objective is to validate compliance with a policy or standard, the penetration test measures the risk associated with an information system.
Realistic conditions
During a penetration test, the steps and techniques of a real malicious actor are reproduced in order to detect potential vulnerabilities
Risk assessment
With our approach, penetration testing can identify vulnerabilities that could be exploited, as well as likely scenarios.
Final Report
This report provides the details required to reproduce the risk situations. It also contains recommendations for the implementation of an action plan.
Conducting an intrusion test
Discovery of the perimeter Gathering information Vulnerability research Building attack scenarios and compromising the IS Initial compromise, access maintenance, and privilege escalation Writing and delivering the report.

Our cybersecurity training courses

1-day cybersecurity training
Data Privacy Professionals offers a 1-day cybersecurity training course. It will enable you to implement digital skills, cyber hygiene, and best practices in cybersecurity.
E-learning cybersecurity
Data Privacy Professionals offers e-learning cybersecurity training courses. This will allow you to train at your own pace.

A local and international company
Data Privacy Professionals provides its services across France and especially in Île-de-France (Parisian region) and the Grand-Est region:
• in Alsace (Bas-Rhin / Haut-Rhin) : Strasbourg, Mulhouse, Colmar.
• in Lorraine (Moselle, Meurthe et Moselle, Meuse, Vosges) : Nancy, Metz, Thionville, Épinal, Saint-Dié, Bar-le-Duc, Forbach, Sarreguemines.
• in Champagne-Ardenne : Reims, Troyes, Charleville-Mézières.
We also intervene abroad (in French, English and German)
