Cybersecurity State
Cybersecurity is crucial in France, Europe, and the world. Governments, businesses, communities, healthcare services, and individuals are all potential victims of ransomware, identity theft, or other cyberattacks, often with disastrous consequences. Hackers primarily seek financial gain, but may also engage in espionage or destabilization activities. They exploit poorly protected, vulnerable, or outdated systems as well as insecure data. Internet users are often weak in digital skills and can fall victim to phishing and other types of fraud. The evolution of new technologies and artificial intelligence has led to increased regulation of data due to its economic value and the growing digitization of society, which can lead to new abuses.
The applicable regulations
The NIS (Network and Information Security) Directives
The NIS Directive 1 is a set of measures related to cybersecurity within the European Union, aimed at strengthening the cybersecurity of “operators of essential services for the functioning of the economy and society.” ANSSI (French National Cybersecurity Agency) will be there to assist these operators when they are victims of a cyberattack.
On January 16, 2023, the NIS Directive 2 was published, and Member States have 21 months to transpose it into their legislation. This directive deepens and widens the scope of cybersecurity. It will come into effect by 2024. The innovations in this directive include a proportionality mechanism that distinguishes between essential and important companies (establishing different requirements for each), and a strengthening of sanctions.
Discover digital regulations.


The Cybersecurity Act
The Cybersecurity Act, which came into effect on June 27, 2019, aims to ensure the proper functioning of the internal market while striving for a high level of cybersecurity, cyber resilience, and trust within the Union (Article 1). It is a real breakthrough for Europe’s strategic autonomy in cybersecurity. This text is the culmination of valuable work by the EU and national cybersecurity agencies.
The Cybersecurity Act consists of two parts:
– The first part formalized the mandate of ENISA (European Union Agency for Cybersecurity) or the European Union Agency for Cybersecurity (Article 3) and strengthened its capacities (Article 6);
– The second legislative framework concerns cybersecurity certification for ICT products, services, and processes (Article 56).
The Cybersecurity Act is the legislative framework for cybersecurity in the European space. The Cybersecurity Act has general and obligatory scope for all Member States. It is a regulation with direct application in all its provisions.
The actors of cybersecurity
ENISA
Within the European Union, ENISA (European Union Agency for Cybersecurity) has a mission to ensure a high level of network and information security. In collaboration with national authorities and European institutions, it aims to develop a culture of information network security throughout the Union.

ANSSI
ANSSI (Agence nationale de la sécurité des systèmes d’information) is a French government agency created in 2009. Its main mission is to detect cyberattacks and notify administrations, military, local authorities, and healthcare institutions, while helping them to secure their information systems. It also encourages the development of an internationally safe, stable, and open cyberspace.

BSI
The mission of BSI (Bundesamt für Sicherheit in der Informationstechnik) in Germany is to provide support for information security, understanding it as a prerequisite for digitization and implementing it independently. It ensures that security aspects are taken into account from the development of information systems and applications.

Cybermalveillance.gouv.fr
The website cybermalveillance.gouv.fr has a mission to assist individuals, businesses, associations, local authorities, and administrations who are victims of cybercrime, inform them about digital threats, and provide them with ways to protect themselves.

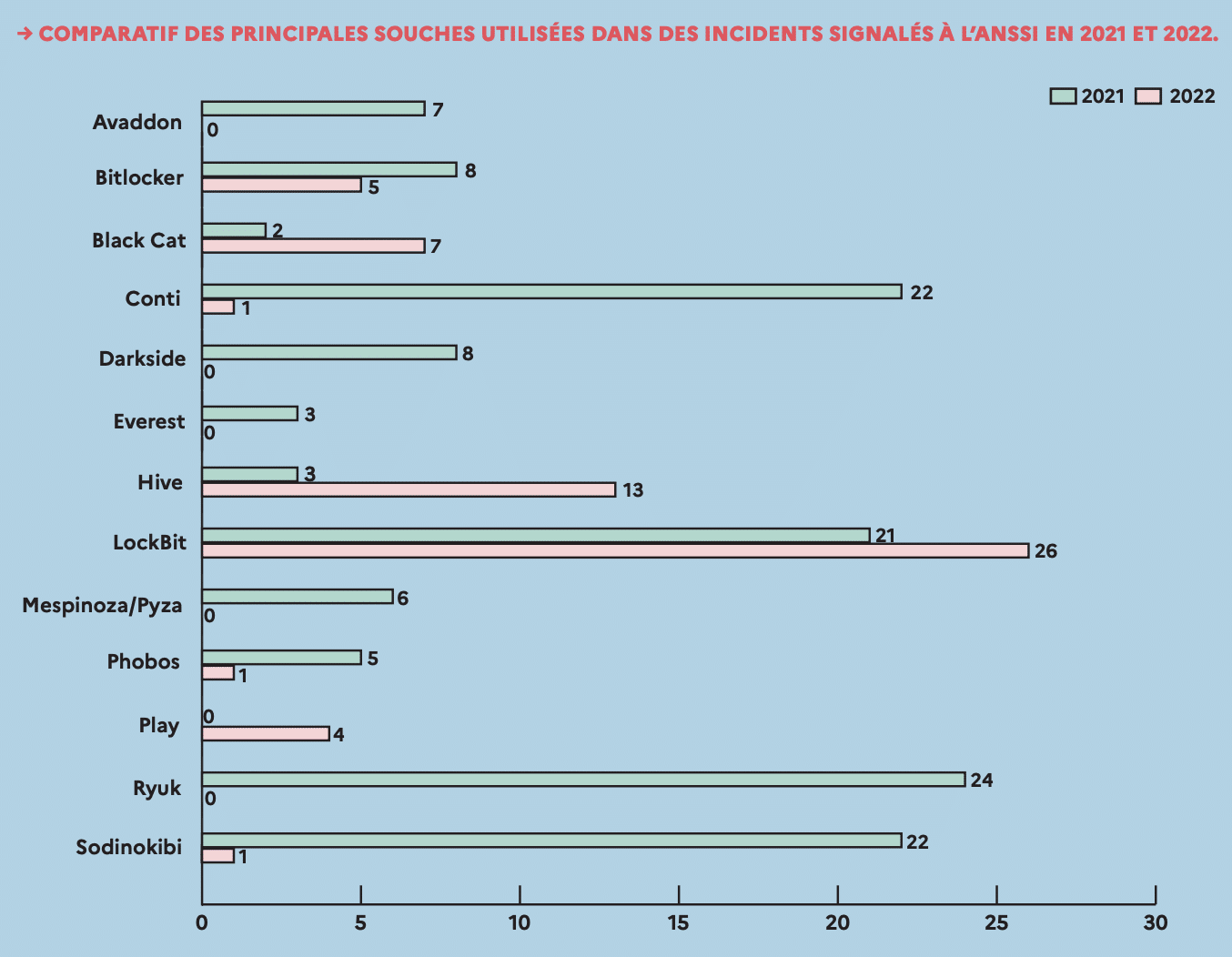
Who are the perpetrators of cyber threats and what are their motivations?
Cyber attackers are individuals or groups seeking to exploit vulnerabilities in an information system for the purpose of causing harm or gaining unauthorized access for personal gain.
There are various types of attacks. The most commonly used ones include:
• Phishing: Phishing is a fraudulent practice of sending emails or messages using well-known services (such as La Poste, a bank, government websites, etc.) to extract sensitive information that allows access to the Information System. New risks have emerged, such as those related to the use of AI.
• Ransomware: Ransomware is a malicious program that aims to block a computer’s resources in exchange for a ransom to unlock it.
• Typosquatting: Typosquatting is a form of cybercrime in which hackers register domains with deliberately misspelled names of known websites.
• Social engineering: Social engineering encompasses techniques used by cybercriminals to persuade unsuspecting users to send them their confidential data, thereby infecting their computers with malware or opening links to infected sites.
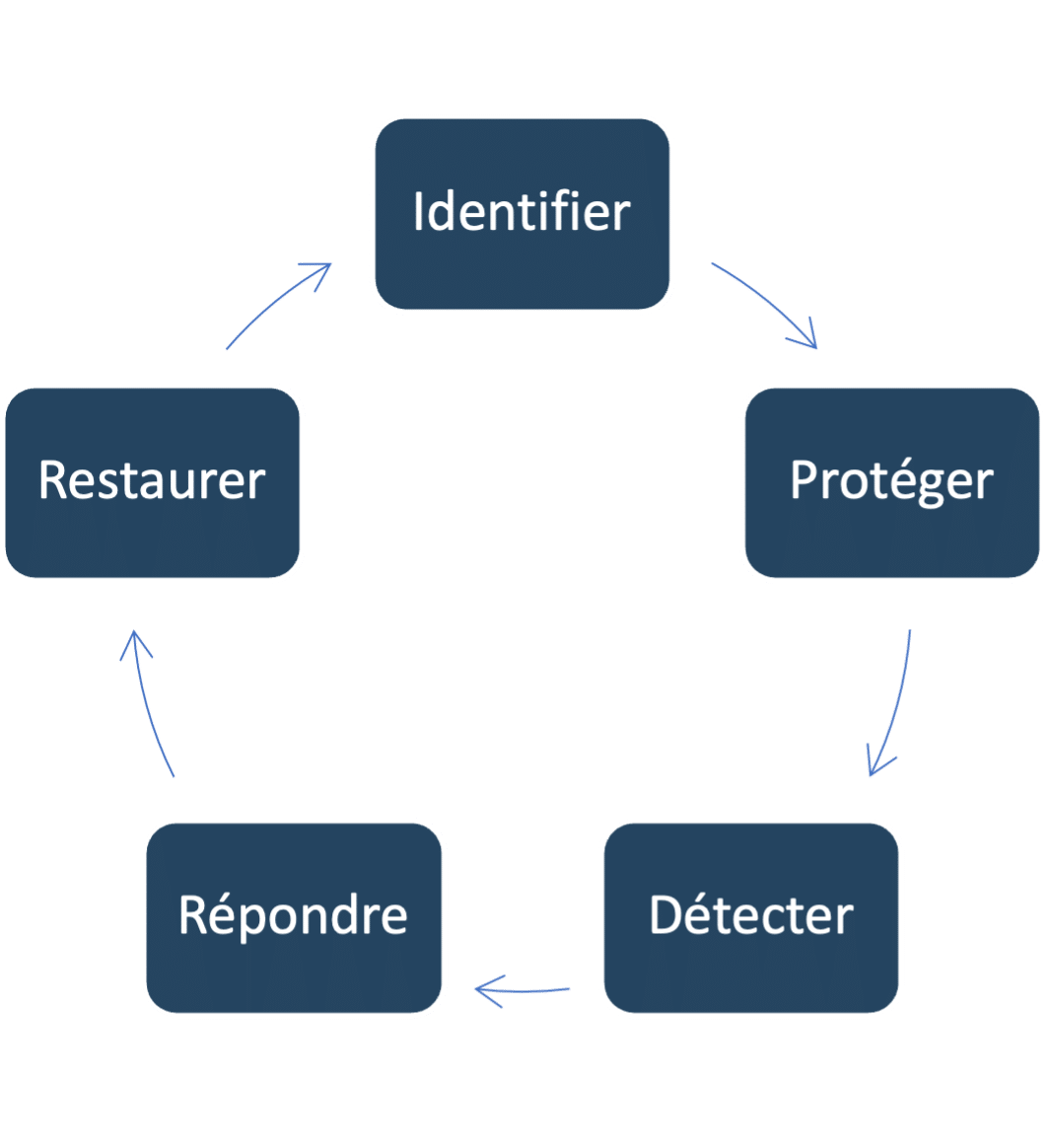
How to protect yourself from cyber threats?
• Identify: Know the critical points of the information system
• Protect: Take necessary corrective measures
• Detect: Diagnose your infrastructure to detect attacks
• Respond: Have an intervention plan
• Restore: Have secure backups and restoration procedures
To face threats, it is necessary to have an up-to-date mapping of the information system, properly identified risks, regularly perform security audits, intrusion tests, and, most importantly, train all staff in cybersecurity.
Implementation of cyber resilience
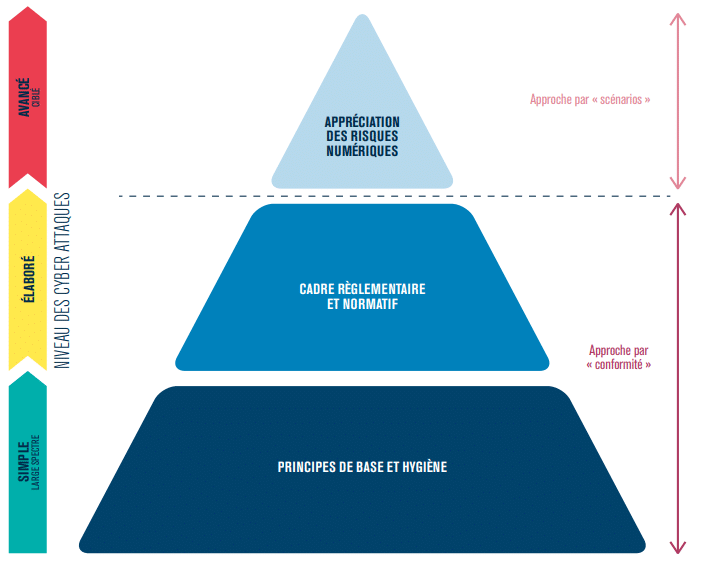
Phase 1: Identification et protection
Perform a risk analysis: The EBIOS RM methodology of ANSSI allows for a cybersecurity risk analysis. It aims to reduce the probability and impact of cyber-attacks by combining compliance and scenario-based approaches. EBIOS RM integrates a dynamic view with attack scenarios, considering both the attacker’s and the company’s perspectives.
Develop and disseminate an information system security policy: The ISSP (Information System Security Policy) is the document that describes the security and cybersecurity policy of the company. It can be static (compliance) or dynamic (considering the attacker). The ISSP may include the following elements:
• Key Performance Indicators (KPIs)
• Service Level Agreements (SLAs)
• Management of authentication and access control
• Architecture diagram
• Knowledge of vulnerabilities
• Detection and incident taxonomy
Phase 2: Threat Detection
Attacker Positioning: Attackers can be internal or external. External penetration testing simulates attacks by anonymous malicious users via an internet connection. Internal penetration testing simulates an attack from one of the company’s internal networks to measure the risks of internal compromise. There are three types of penetration testing:
• Black box: These are the conditions closest to an external attack perpetrated by an unknown attacker. No information is provided.
• Grey box: Limited information is communicated before the start of the test.
• White box: Maximum information is provided before the start of the test, making the target’s operation visible.
Stay Informed About Cyber Threats: There are several information sites on which to stay informed about cyber threats, including:
• The CERT website
• The Bleepingcomputer website
If you have already been a victim of ransomware: To learn more about the ransomware that infected your system, the solution is to use Idransomware.


Phase 3: Respond and Restore
The BCP (Business Continuity Plan) includes a set of procedures, means, equipment, and architectures required to enable the continuity of a company’s activity regardless of the disasters that may occur.
A DRP (Disaster Recovery Plan) refers to various procedures (technical, organizational, security) that enable a company to anticipate, rebuild and restart an information system in the event of a significant disaster or critical incident.